Introduction
In the modern, data-driven world, individuals and organizations actively use web scraping to gather critical information from the web for market research, trend analysis, and other varied purposes. However, traditional methods of web scraping often face bottlenecks such as IP blocks or rate limitations. A practical way to overcome these challenges is to set up a Tor Proxy for Web Scraping, which provides anonymity and easy rotation of IP addresses, streamlining the data-gathering process.
Web scraping involves sending repeated requests to a target website for extracting useful information, but many websites monitor and block that, particularly when multiple requests come from one IP address. That’s where Tor comes in handy. Tor stands for The Onion Router: free software that allows anonymous communication over the Internet by routing requests through a large number of nodes. That makes it impossible for websites to trace your activity or block your IP.
Tor will let you automatically rotate the IP address to avoid IP bans and continuously access data. Using Tor for scraping will also give you a bonus in privacy-the anonymization of traffic. This means that your actual IP will not be disclosed, which is really useful if you don’t want it noticed or you are taking care of privacy during your scrape.
The article will walk you through the process of setting up a Tor proxy server on your localhost and using it in your web scraping projects. In this article, you will go through how to enhance your scraping capabilities while keeping your privacy intact and minimizing the risk of getting blocked by target websites.
Topics to cover to Set up Tor Proxy for Web Scraping:
- What Tor is and why it’s a godsend for web scraping.
- How to set up a local Tor proxy server using Docker.
- How to configure Tor and generate a hashed password for safe control.
- Running Tor Proxy Server and Usage in Python Scripts for Web Scraping.
- Common Issues and Troubleshooting Tips.
- Legal and Ethical Considerations While Scraping with Tor.
By the end of this article, you will know everything about how to leverage Tor for web scraping effectively.
What is Tor and Why use it for Web Scraping?
Basically, Tor is a decentralized network, the main aim of which would be to bring privacy and anonymity to users browsing the internet. Coming from the U.S. Naval Research Laboratory, Tor makes provision for users to communicate and access the internet without showing their identity. This is achieved by routing the internet through several volunteer-operated servers in such a way that the origin and destination of the data remain hidden.
Tor works by encrypting your internet traffic and sending it through multiple nodes before it actually reaches its final destination. Each time data passes through a node, a layer of encryption is removed, and this process continues until it finally reaches its destination, much like peeling an onion-hence the name “The Onion Router.” This multi-layered encryption ensures that no single node knows both the source and the destination of the traffic, making it very hard to trace the original sender.
In web scraping, the following are the key advantages of Tor,
Anonymity:
Websites use ways to trace and block scrapers, such as blocking specific IP addresses after a certain number of requests. To that regard, Tor anonymizes your traffic, this greatly reduces the likelihood of websites detecting and blocking your scrapers easily.
Ip Rotation:
In web scraping, one of the most challenging tasks consists of IP bans. Tor rotates IP addresses using different exit nodes. Therefore, you have a chance to make more requests since the website sees requests from multiple IP addresses.
Access to Geo-Blocked Content:
Some websites run content only for specific geographic locations. This is called geo-blocking. Using Tor, on the other hand, allows users to select exit nodes from randomized locations and users then can access such content from regions it might be blocked.
Set up Tor Proxy Server for Web Scraping
This section will walk us through setting up the Tor proxy server locally. We are going to use Docker for easy and repeatable installation. It involves the creation of the Docker container for Tor, configuration files, and ensuring all the dependencies that are required are in place.
Requirements
In general, to get started, you would need the following tools/softwares to be installed on your local machine:
- Docker: Docker will provide an enclosed environment to run Tor in and make setup quite easy. You can download and install Docker from the official Docker website.
- Python: Python will be used later to run our web scraping script using the Tor proxy. You can download and install Python from the official Python website.
- Tor: The Tor network provides the backbone for all of this, enabling us to route traffic anonymously. Dockerfile will install this within docker container. For more information about Tor, visit the official Tor Project website.
Let’s dive into creating the Dockerfile and generate_torrc.sh files. We will add all the instructions to the Dockerfile to setup tor server for us.
Dockerfile
# Stage 1: Generate the hashed password
FROM alpine:latest as builder
# Install Tor
RUN apk update && apk add tor
# Generate the hashed password and save it in a file
RUN tor --hash-password Your_Password > /hashed_password.txt
# Stage 2: Set up Tor with the hashed password
FROM alpine:latest
# Install Tor and other necessary tools
RUN apk update && apk add tor busybox-suid
# Copy the hashed password from the builder stage
COPY --from=builder /hashed_password.txt /hashed_password.txt
# Copy the script to generate torrc
COPY generate_torrc.sh /generate_torrc.sh
# Make the script executable
RUN chmod +x /generate_torrc.sh
# Run the script to generate the torrc file
RUN /generate_torrc.sh
# Expose necessary ports
EXPOSE 12453 12454
# Print files for verification and run Tor
CMD ["sh", "-c", "cat /hashed_password.txt; cat /etc/tor/torrc; tor"]
This Dockerfile has a multi-stage build, generating the hashed password in a safe way from which the final setup could use. Replace the Your_Password with your password to generate the appropriate hash in the Dockerfile.
TORRC Configuration File:
The torrc file is the configuration file that is used by the Tor to control various parameters. In our setup, we’ll make use of the generate_torrc.sh script to create the torrc file dynamically.
generate_torrc.sh
#!/bin/sh
HASHED_PASSWORD=$(tail -n 1 /hashed_password.txt)
echo "Hashed password is: ${HASHED_PASSWORD}"
echo "SocksPort 0.0.0.0:12453" > /etc/tor/torrc
echo "ControlPort 0.0.0.0:12454" >> /etc/tor/torrc
echo "HashedControlPassword ${HASHED_PASSWORD}" >> /etc/tor/torrc
echo "CookieAuthentication 0" >> /etc/tor/torrc
Let’s dive into the important parameters the script will add to the torrc configuration file,
SocksPort: This defines the port used for handling SOCKS requests. The script sets this to 0.0.0.0:12453, allowing Tor to accept requests on port 12453 from any IP address (In this case any ip address from our local network).
echo "SocksPort 0.0.0.0:12453" > /etc/tor/torrcControlPort: The control port allows external applications (e.g., Python scripts) to communicate with Tor for operations like changing circuits. In our setup, it is set to 0.0.0.0:12454. We will be using this to rotate proxies or request new IPs.
echo "ControlPort 0.0.0.0:12454" >> /etc/tor/torrcHashedControlPassword: For security, instead of providing a plaintext password, we will be using a hashed password for authentication on the control port. The hashed password is generated and stored in /hashed_password.txt, and the script reads it to add it to the torrc file.
echo "HashedControlPassword ${HASHED_PASSWORD}" >> /etc/tor/torrcCookieAuthentication: This setting disables cookie-based authentication, so that the system can use hashed password instead.
echo "CookieAuthentication 0" >> /etc/tor/torrcThe generate_torrc.sh file puts all the configurations to the torrc file, allowing us to configure the Tor proxy server efficiently.
Build and Run the Docker Image
Build the Image: Make sure to keep the Dockerfile and the generate_torrc.sh in the same directory and open the terminal in the same directory. Now run below command to build the docker image.
docker build -t tor-proxy .Run the Container: After building the image, run the container using below command.
docker run -d -p 12453:12453 -p 12454:12454 --name tor_proxy tor-proxyThis command runs the Tor proxy server in the background (-d flag) and exposes the necessary ports.
Set up a Python Script to Test the Tor Proxy Server
Once the Tor proxy server is up and running, you can then configure the web scraping script to make use of the Tor proxy for sending requests anonymously. Below, we’ll walk through how you can set up a Python script using the Tor proxy, that includes rotating the IP addresses to avoid detection.
To interact with the Tor proxy, we will use Python with the requests and stem libraries. First, you need to create a requirements.txt file with the following dependencies:
requests
stem
requests[socks]
Install the necessary Python libraries with:
pip install -r requirements.txt
Here’s an example Python script to use Tor as a proxy for web scraping:
tor_test.py
import requests
def get_ip():
proxy = {
'http': 'socks5h://<your_private_ip>:12453',
'https': 'socks5h://<your_private_ip>:12453'
}
try:
response = requests.get('http://httpbin.org/ip', proxies=proxy)
return response.json()
except requests.RequestException as e:
print(f"Error: {e}")
return None
if __name__ == "__main__":
ip_info = get_ip()
if ip_info:
print(f"Current IP: {ip_info['origin']}")
In this script, we specify the SOCKS5 proxy provided by Tor, using socks5h://<your_private_ip>:12453 to route all requests through Tor. This helps in masking our IP address, as each request made through Tor will use a different exit node, thus providing a new IP address.
Rotating IP Addresses
To rotate IP addresses and avoid IP bans, you can use Tor’s control port to request a new identity. This is useful in web scraping to avoid getting blocked by servers that enforce rate limits or detect multiple requests from the same IP.
To change Tor circuits and get a new IP, use the following Python script, which sends a signal to the Tor control port:
import requests
import stem
import stem.connection
from stem.control import Controller
import time
def rotate_ip():
with Controller.from_port(address="<your_private_ip>", port=12454) as controller:
controller.authenticate(password='Your_Password')
controller.signal(stem.Signal.NEWNYM)
print("New Tor IP requested.")
def get_ip():
proxy = {
'http': 'socks5h://<your_private_ip>:12453',
'https': 'socks5h://<your_private_ip>:12453'
}
try:
response = requests.get('http://httpbin.org/ip', proxies=proxy)
return response.json()
except requests.RequestException as e:
print(f"Error: {e}")
return None
if __name__ == "__main__":
for _ in range(5):
ip_info = get_ip()
if ip_info:
print(f"Current IP: {ip_info['origin']}")
rotate_ip()
time.sleep(5) # to ensure tor gets enough time to get a new IP.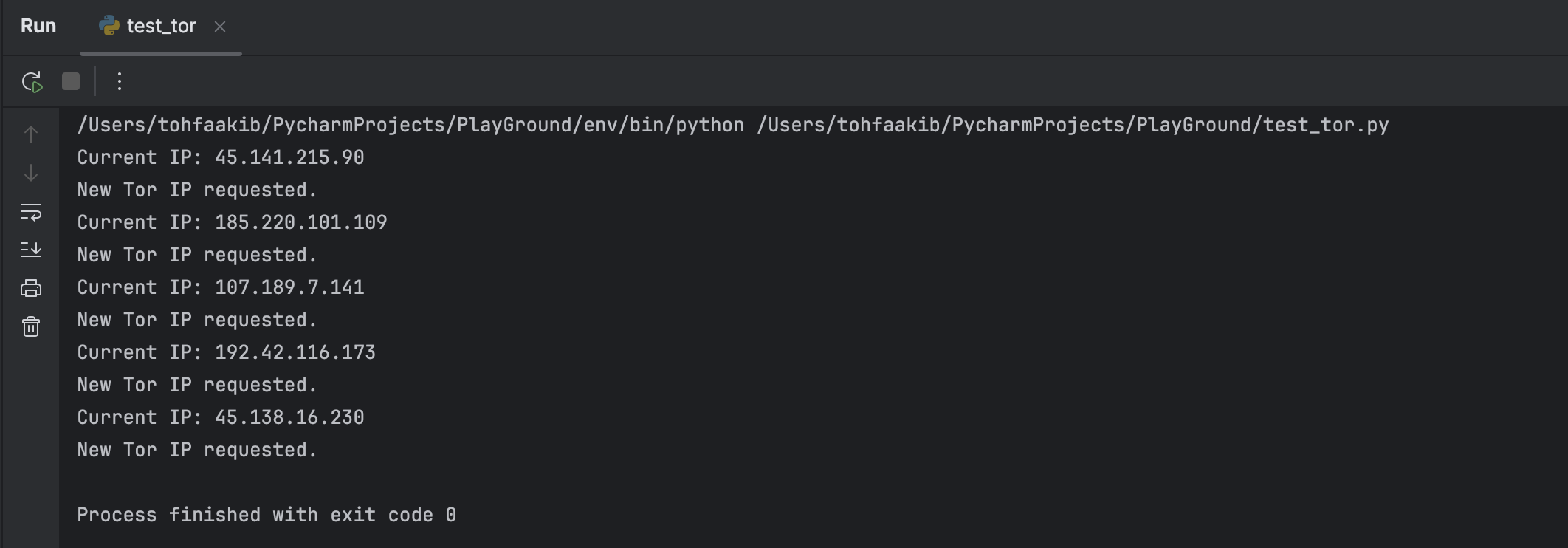
In this script:
rotate_ip(): Connects to the Tor control port and sends aNEWNYMsignal to request a new identity, which effectively changes the IP address for subsequent requests.- Control Port Authentication: The script uses
Your_Passwordto authenticate with the Tor control port. Make sure to replace it with the password you used in Dockerfile when setting up Tor. <your_private_ip>": This is the private ip of or your local machine. Use,ifconfigcommand in linux or macos and useipconfigcommand in windows to find the private ip of your local machine.
Common Issues and Troubleshooting for Tor Proxy for Web Scraping
While setting up and using Tor as a proxy for web scraping, you may encounter some common issues. Here are the most frequent problems and their solutions:
- Tor Control Port Authentication Failure:
- Issue: The Python script fails to authenticate with the Tor control port.
- Solution: Ensure that the password in the Python script matches the one you set in the
generate_torrc.shfile. If you updated the password, make sure the script and configuration files are consistent.
- Tor Circuit Not Changing:
- Issue: Even after requesting a new identity, the IP address does not change.
- Solution: Make sure there is enough time between requests for a new circuit. Tor might need some time to establish a new circuit, and requesting a new IP too frequently might return the same IP.
- Tip: Increase the delay time if you notice that the IP is not changing as expected.
- Slow Performance:
- Issue: Using Tor for web scraping can be slower than using a direct connection.
- Solution: This is an expected behavior due to the nature of the Tor network, which routes traffic through multiple relays. To mitigate this, reduce the frequency of requests and use caching when possible to avoid making unnecessary repeated requests.
- Docker Network Issues:
- Issue: The Docker container cannot connect to external websites.
- Solution: Ensure that Docker has proper network access. Check if there are any firewall rules or network restrictions that could be preventing the container from accessing the internet.
- Port Conflicts:
- Issue: Ports
12453or12454are already in use by another application. - Solution: Modify the ports in the Docker run command to use different, available ports. For example:
docker run -d -p 12500:12453 -p 12501:12454 --name tor_proxy tor-proxyThen, update your Python script to use the new ports.
- Issue: Ports
Legal and Ethical Considerations for Tor Proxy for Web Scraping
When using Tor for web scraping, it’s important to consider both legal and ethical implications:
- Terms of Service: Always review and comply with the website’s terms of service. Many sites prohibit automated scraping, and ignoring these rules can lead to legal consequences.
- Privacy and Respect: Using Tor provides anonymity, but we shouldn’t scrape website or data irresponsibly. Avoid scraping sensitive or personal information without permission.
- Network Impact: The Tor network is a shared public resource. Excessive usage, such as high-frequency scraping, can place strain on the network. Use Tor responsibly to avoid negatively impacting others.
Respect the ethical guidelines and always ensure that your activities do not violate any laws or impact others adversely.
Conclusion
In this article, we have walked through the setup of a Tor proxy server on Docker, configuring it for web scraping, and handling IP rotation. Using Tor allows you to have anonymity, which is very crucial for avoiding IP ban during the scraping process. We also went through some common issues and provided troubleshooting tips to make sure everything went seamlessly.
Keep in mind that there are both ethical and legal considerations surrounding the use of Tor and web scraping, thus, you should be responsible in using this setup and, at all times, strictly observe any terms of service when interacting with any website. Happy scraping!

